
BACKGROUND IMAGE: iSTOCK/GETTY IMAGES
identity management (ID management)
Identity management (ID management) is the organizational process for identifying, authenticating and authorizing individuals or groups of people to have access to applications, systems or networks by associating user rights and restrictions with established identities. The managed identities can also refer to software processes that need access to organizational systems.
Identity management includes authenticating users and determining whether they're allowed access to particular systems. ID management works hand-in-hand with identity access management systems. Identity management is focused on authentication, while access management is aimed at authorization.
ID management determines whether a user has access to systems, but also sets the level of access and permissions a user has on a particular system. For instance, a user may be authorized to access a system but be restricted from some of its components.
The main goal of identity management is to ensure that only authenticated users are granted access to the specific applications, systems or IT environments for which they are authorized. This includes control over user provisioning and the process of onboarding new users such as employees, partners, clients and other stakeholders. Identity management also includes control over the process of authorizing system or network permissions for existing users and the offboarding of users who are no longer authorized to access organization systems.
Identity governance, the policies and processes that guide how roles and user access should be administered across a business environment, is also an important aspect of identity management. Identity governance is key to successfully managing role-based access management systems.
Importance of identity management
Identity management is an important part of the enterprise security plan, as it is linked to both the security and productivity of the organization.
In many organizations, users are granted more access privileges than they need to perform their functions. Attackers can take advantage of compromised user credentials to gain access to organizations' network and data. Using identity management, organizations can safeguard their corporate assets against many threats including hacking, ransomware, phishing and other malware attacks.
Identity management systems can add an additional layer of protection by ensuring user access policies and rules are applied consistently across an organization.
An identity and access management (IAM) system can provide a framework that includes the policies and technology needed to support the management of electronic or digital identities. Many of today's IAM systems use federated identity, which allows a single digital identity to be authenticated and stored across multiple disparate systems.
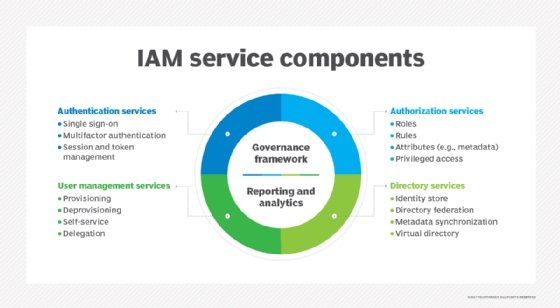
An IAM system can also be used to deploy single sign-on (SSO) technologies to significantly decrease the number of passwords users need; SSO incorporates a federated-identity approach by using a single login and password to create an authentication token that can be accepted by various enterprise systems and applications. Combined with multifactor authentication as well as enforceable security policies such as the principle of least privilege, which gives users only the access they require to fulfill their roles, enterprises can lower the risk of security breaches.
Challenges of implementing identity management
To successfully implement identity management, an enterprise must be able to plan and collaborate across business units. Organizations that establish identity management strategies with clear objectives, defined business process and buy-in from stakeholders at the outset will more likely be successful. Identity management works best when IT, security, human resources and other departments are involved.
Identity management systems must allow companies to automatically manage multiple users in different situations and computing environments in real time. It's just not feasible to manually adjust access privileges and access controls for hundreds or thousands of users. Additionally, authentication must be simple for users to perform, easy for IT to deploy and secure.
One of the top challenges of implementing identity management is password management. The functions of creating, updating and deleting passwords can have real costs that organizations want to reduce. Consequently, IT professionals should investigate techniques that can reduce the impact of these password issues in their companies.
For security reasons, tools for managing identity management should run as an application on a dedicated network appliance or server, either on premises or in the cloud. At the core of an identity management system are policies defining which devices and users are allowed on the network and what a user can accomplish, depending on device type, location and other factors. All of this also depends on appropriate management console functionality, including policy definition, reporting, alerts, alarms and other common management and operations requirements. An alarm might be triggered, for example, when a specific user tries to access a resource for which they do not have permission. Reporting produces an audit log documenting what specific activities were initiated.
Many identity management systems offer directory integration, support for both wired and wireless users, and the flexibility to meet almost any security and operational policy requirement. Because bring your own device (BYOD) is so strategic today, time-saving features such as automated device onboarding and provisioning, support for a variety of mobile operating systems and automated device status verification are becoming common.
Business benefits of identity management
In addition to managing employees, the use of identity management along with access management enables a business to manage customer, partner, supplier and device access to its systems while ensuring security is the top priority.
This goal can be accomplished on several fronts, starting with allowing authorized access from anywhere. As people increasingly use their social media identities to access services and resources, organizations must be able to reach their users through any platform, allowing them to access corporate systems through their existing digital identities.
Identity management can also be used to improve employee productivity, which is especially important when onboarding new employees, or changing authorizations for accessing different systems when an employee's function changes. When companies hire new employees, they have to be given access to specific parts of their systems, given new devices and provisioned into the business. Done manually, this process can be time-consuming and reduces the ability of the employees to get right to work. However, automated provisioning can enable companies to accelerate the process of allowing new employees to access the required parts of their systems.
Finally, identity management can be an important tool for enhancing employees' user experience, especially for reducing the impact of identity chaos, the state of having multiple sets of user IDs and passwords for disparate systems. Typically, people can't remember numerous usernames and passwords and would prefer to use a single identity to log in to different systems at work. SSO and unified identities enable customers and other stakeholders to access different areas of the enterprise system with one account, ensuring a seamless user experience.









Join the conversation
5 comments